CimTrak for Active Directory
Active Directory (AD) and LDAP: Monitor for Changes

WHAT WE MONITOR




Large environments can suffer from alterations and changes that fly under the radar. Unexpected AD or LDAP changes may be simple and limited to a single entity, such as adding a new file system, account, or network resource. The broader impact, such as denial of service, could be the result depending upon the hierarchical design. CimTrak provides the awareness to quickly detect and alert when such deviations occur.
Benefits of Using CimTrak for
Active Directory
Active Directory
Detect changes to objects, attributes, and schema
Side-by-side comparison for easy identification of change
Restore a previous configuration when necessary
CimTrak for Active Directory/LDAP Can:
-
Detect when an entity has been added to or deleted from the domain, log the activity, and notify the responsible parties by e-mail, Syslog, or SNMP.
-
Detect, log, and notify when its configuration has been modified, added, or deleted.
-
Detect, log, and notify when any content has been modified, added to, or deleted from the directory’s database.
-
Detect, log, and notify when any of the directory’s schema entities have been modified, added, or deleted.
How CimTrak for Active Directory/LDAP Works:
When changes are made to any number of the AD/LDAP objects, attributes, and schema, the changes will be detected and alerts generated instantaneously. Those same alerts can be resolved and remediated within the CimTrak console or can be fed into a SIEM or a trouble ticking system for centralized management.
When CimTrak locks an LDAP installation for monitoring, it reads the entire contents of the directory database. It calculates a digital signature for each member, configuration, or schema entity and stores it in CimTrak’s master repository along with a copy of the entity itself.
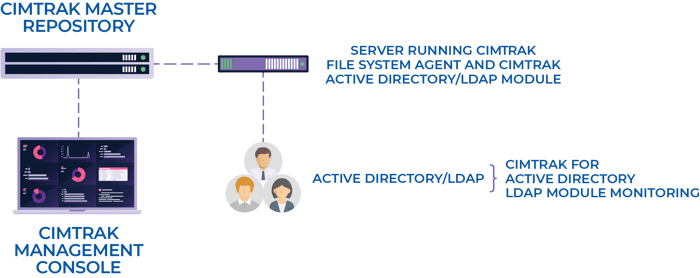
At user-configured intervals, CimTrak reads the contents of the directory database, calculates the digital signature of each entity, and compares it to the signature stored in CimTrak’s master repository.
When CimTrak detects a changed (or an added or deleted) entity, the entity and its digital signature is then stored in the master repository. The master repository then logs the detected change and sends notifications to the configured emails and/or configured Syslog services and/or SNMP services.
Active Directory
Action: The threat actor changes the account password
Impact: When the threat actor changes the compromised account's password, that prevents the real user from gaining access again.
Action: The threat actor deletes all other domain administrators in the domain admin group.
Impact: When the actor removes all other domain administrators, this prevents other admins from locking down the environment and stopping the threat actor.
Action: Modifies and deletes DNS entries in the domain controller.
Impact: When the threat actor makes changes to the DNS, this prevents many web tools to stop resolving in the browser preventing user access, and causes many production servers to stop communicating - resulting in downtime.
LDAP
Action: The threat actor uses an LDAP Injection method to elevate the privileges of this account to view all security level objects.
Impact: When the actor uses the LDAP Injection to increase privileges, this gives them access to all configurations and settings. Information and Resources can be gathered and stolen with this access.
Action: The threat actor adds this account to the NetSec group.
Impact: When the actor adds this account to the NetSec group, this allows the account to pass authentication to particular tools integrated with this access control. The actor would also be able to see and disable all other administrators.



